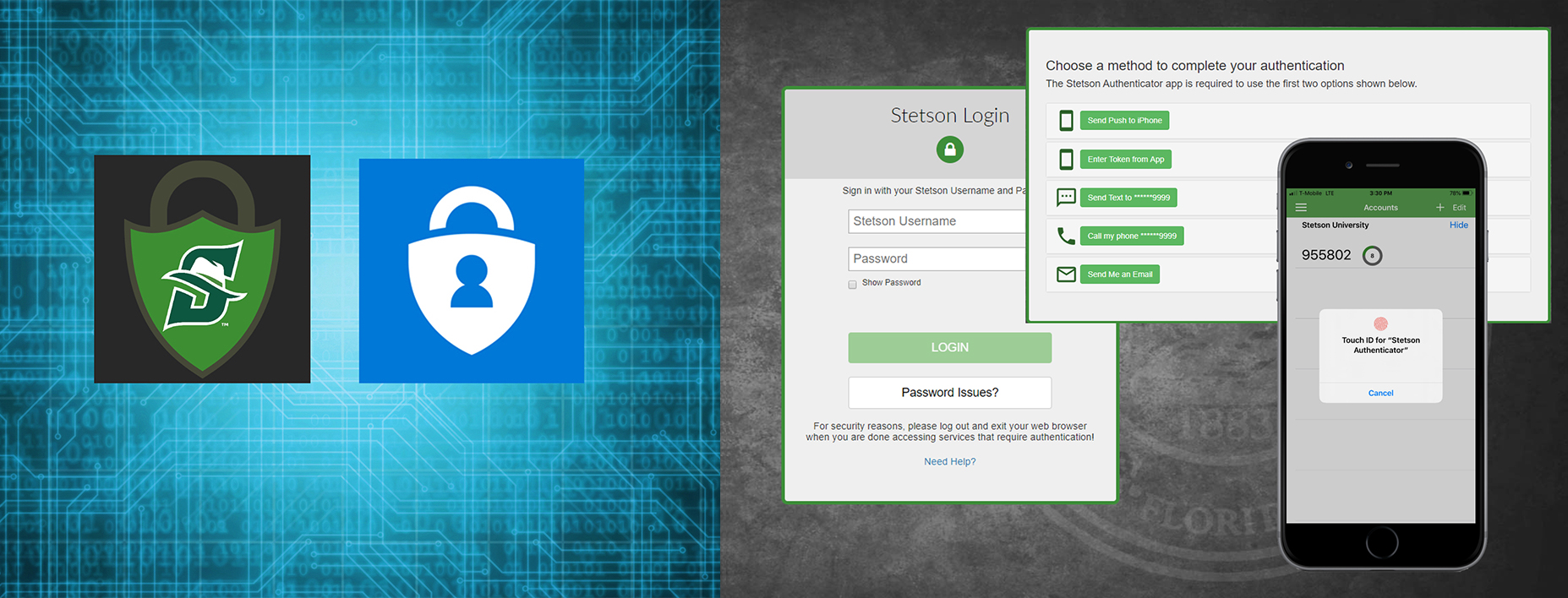
How to implement a vulnerability management program for your organization. | Brian Busto posted on the topic | LinkedIn

Joe Wagner - Director of Cybersecurity Operations / Threat Investigations Lead - Stetson CyberGroup | LinkedIn

Cybersecurity program can succeed when Governance is discussed, defined, and executed. #cybersecurity #hacking #security #technology #informationsecurity # | Brian Busto posted on the topic | LinkedIn

Cerini Connection: What You Need To Know To Create a Successful Cyber Program - Cerini & Associates, LLP